
DEFINISI DATA FORGERY | All About Data Forgery

DATA FORGERY DESTY PUTRI RASMAWATI FIENDRA RAHMAWAN - ppt download

Data Forgery | Dunga Ashola

Etika Profesi Teknologi & Informasi: Data Forgery

Data Forgery – BOCAH PECANDU TEKNOLOGI INFORMASI

Data Forgery | Faisal Hidayatullah

Cyber Crime Notes: Data Forgery

Data Forgery - Tugas Etika Profesi TIK

Data Forgery: Contoh kejahatan Data Forgery (kilik bca)

ETIKA PROFESI TEKNOLOGI INFORMASI KOMUNIKASI Carding Data Forgery

Data Forgery Images, Stock Photos & Vectors | Shutterstock

Data Forgery – Just Another Random Blogs

Data Forgery Images, Stock Photos & Vectors | Shutterstock

Beragam Kejahatan Siber Menyerbu Indonesia - News Liputan6.com
What is SSRF (Server-side request forgery)? Tutorial & Examples | Web Security Academy

Cloud Computing Internet Security Cross-site Request Forgery Data Web Application Security, PNG, 768x619px, Cloud Computing,

Data Forgery | Velonica

Data Forgery Images, Stock Photos & Vectors | Shutterstock

Server-Side Request Forgery Exposes Data of Technology, Industrial and Media Organizations

DOC) Makalah EPTIK Pertemuan 11 ‘‘DATA FORGERY” | Ben Wau - Academia.edu
Data Forgery Pada E-Banking BCA - SIM | PDF

DATA FORGERY, CYBER-ESPINAGE, SABOTAGE dan EXTORTION by putri puput

MAKALAH ETIKA PROFESI TEKNOLOGI INFORMASI & KOMUNIKASI (EPTIK) “DATA FORGERY” – Page 4 – Kelas Hebat

Etika Profesi TEKNOLOGI INFORMASI & KOMUNIKASI - ppt download

Pengertian Illegal Content - ILLEGAL CONTENT, DATA FORGERY & CYBER ESPIONAGE

ETIKA PROFESI “DATA FORGERY"Tema Perusak website Komisi Pemilihan Umum (KPU) - YouTube

forgery Free Photos, Icons, Vectors & Videos | Freestock

TUGAS UAS EPTIK : “DATA FORGERY” – Kelas Hebat

data forgery/pemalsuan data dalam cybercrime - YouTube

Data Forgery | LIDYA ULVA DWI SEPTIYOWATI

Kasus Kejahatan Komputer Wajah Kasus di Indonesia pernah

Makalah Cybercrime (Data Forgery Dan Cyber Espionage) Halaman 2 - Kompasiana.com

Gambar Data Forgery

Dosen Kriminolog UI: Kejahatan siber marak pada masa pandemi - ANTARA News

A Pentester’s Guide to Cross-Site Request Forgery (CSRF) | Cobalt.io | Cobalt Blog

Pengertian Illegal Content - ILLEGAL CONTENT, DATA FORGERY & CYBER ESPIONAGE

Pemalsuan Data (Data Forgery)

CEEOL - Article Detail

Data-link message attack tree. M1: monitoring attack; M2: data forgery… | Download Scientific Diagram
Data Forgery | PDF

Kelompok IT by Mia Anastasia

ModusModus Kejahatan Dalam Teknologi Informasi Latar Belakang ICT

PPT - E tika Profesi TEKNOLOGI INFORMASI & KOMUNIKASI PowerPoint Presentation - ID:4069152
![Web viewContoh Kasus Data Forgery. Diperoleh 03 Mei 2014, dari Biografi Ray Indra Taufik Wijaya - [DOCX Document]](https://i2.wp.com/demo.fdokumen.com/img/378x509/reader025/reader/2021051206/5c79da0f09d3f27b458ca164/r-2.jpg)
Web viewContoh Kasus Data Forgery. Diperoleh 03 Mei 2014, dari Biografi Ray Indra Taufik Wijaya - [DOCX Document]

Tugas EPTIK

Waspada Kejahatan SIM Swap, Jangan Bagikan Kode OTP! – Diskominfo Bulungan

Kesimpulan Tugas KAB “Data Forgery | Yanti Mulyanti - Academia.edu
DATA FORGERY

Pertemuan 4 Dwi hartanto S Kom Pembahasan 1

Komputer dan kejahatan (CYBER CRIME)

APA ITU DATA FORGERY? | UBSI KAMPUS KOTA SUKABUMI – CampusNews.co.id
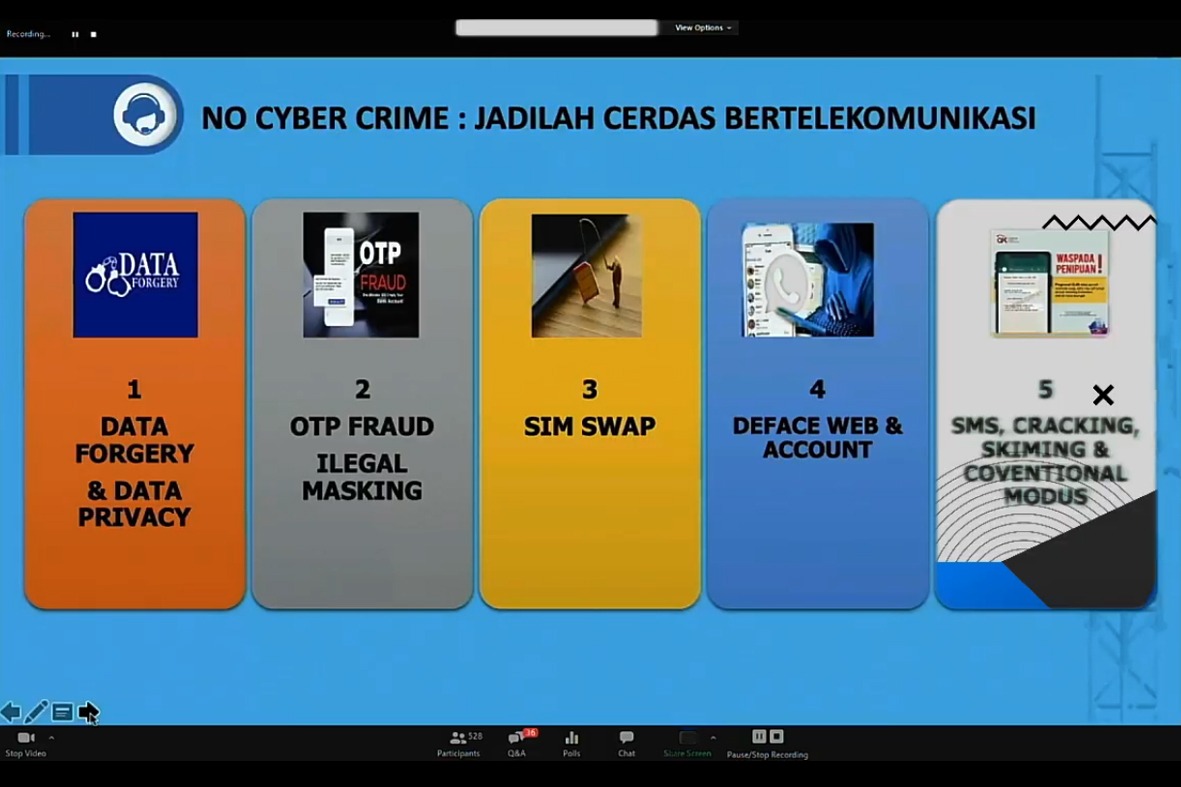
Waspada Kejahatan SIM Swap, Jangan Bagikan Kode OTP!

Data Forgery - Etika Profesi Teknologi Informasi dan Komunikasi - YouTube

What is server-side request forgery (SSRF)? | Netsparker

contoh data forgery | Sistem Informasi Hukum

Snapshot of the fourth sample of skilled forgery-Position(sensor) data… | Download Scientific Diagram

NRS 205.481 Forgery by creation, alteration or deletion of data, information, image, program in computer

Kejahatan Siber Marak pada Masa Pandemi Covid-19 - Nasional - AnalisaDaily.com

Data forgery detection for vehicle black box | Semantic Scholar

FORGERY - criminal concept stock illustration. Illustration of creative - 160422820
![]()
Data Forgery Images, Stock Photos & Vectors | Shutterstock
![Thread by @EPsYOUNGK, 𝗡𝗘𝗧𝗜𝗤𝗨𝗘𝗧𝗧𝗘: 𝙋𝙚𝙧𝙣𝙖𝙝 𝙂𝙖𝙠, 𝙊𝙥𝙚𝙣 𝙈𝙞𝙣𝙙𝙚𝙙? ━━━ Studi mengenai penggunaan sosial media pada […]](https://i1.wp.com/pbs.twimg.com/media/EtCWi18UUAQLVza.jpg)
Thread by @EPsYOUNGK, 𝗡𝗘𝗧𝗜𝗤𝗨𝗘𝗧𝗧𝗘: 𝙋𝙚𝙧𝙣𝙖𝙝 𝙂𝙖𝙠, 𝙊𝙥𝙚𝙣 𝙈𝙞𝙣𝙙𝙚𝙙? ━━━ Studi mengenai penggunaan sosial media pada […]

Makalah Data Forgery.docx - MAKALAH DATA FORGERY Diajukan untuk memenuhi nilai tugas pada matakuliah Etika Profesi Teknologi Informasi dan Komunikasi | Course Hero

Pp eptik

CYBER CRIME Cyber Crime Sebuah Evolusi Kejahatan Jenis

Using AI, Israel’s Aperio protects infrastructure from hackers | The Times of Israel

13 Jenis Cyber Crime, Kejahatan Internet yang Merugikan - Cermati.com

Kriminal Tekhnologi: Definisi Data Forgery

Data forgery detection for vehicle black box | Semantic Scholar

Are your critical systems lying to you? Protecting SCADA Systems from Data Forgery - Cyber Defense Magazine

Digital Images Forgery Detection Techniques: Develop An Active Approach Based on Cellular Automata and Data Embedding in Spatial Domain: 9783847321422: Computer Science Books @ Amazon.com

PPT - Pertemuan 4 PowerPoint Presentation, free download - ID:1995127

Dua Sisi Layanan Telekomunikasi

Makalah Etika Profesi TI Illegal Content dan Data Forgery - PDF Free Download

FORGERY - criminal concept stock illustration. Illustration of forgery - 160082326

APERIO Systems’ patent-pending Data Forgery Protection™ technology is the first cybersecurity solution that detects artificial manipulations of industrial process data, enabling operators to take real-time corrective action without service disruption …

Cross-Site Request Forgery (CSRF): Impact, Examples, and Prevention
Vault Infosec - Server Side Request Forgery - Abusing the Functionality of Server | Facebook

Tinjauan Regulasi Kejahatan di Internet 1 Cybercrime

Flowchart of image forgery detection and localization using proposed… | Download Scientific Diagram

data forgery by Vanessa Julianne Manalu
Penyembunyian Data Untuk Seluruh Ekstensi File Menggunakan Kriptografi Vernam Cipher dan Bit Shiffting

Forgery PNG Images, Transparent Forgery Images
Keamanan Aplikasi Web Melalui Penerapan Cross Site Request Forgery(CSRF) Latar Belakang

Pengertian Illegal Content - ILLEGAL CONTENT, DATA FORGERY & CYBER ESPIONAGE

Tugas EPTIK
39,031 Forgery Stock Videos and Royalty-Free Footage - iStock

Ancaman dan Kasus Kejahatan Elektronik SI 703 Hukum

Blockchain | business | Sourcefarm

Sejumlah Jenis Kejahatan Siber di Indonesia

Cross-Site Request Forgery (CSRF) | by Sadeepa Gayashan | Medium
Tugas Pertemuan 11 Kelompok 1 12.6B.35 | PDF

Detecting photo forgery

Security | HR & Payroll and blockchain | Proofeasy
Paper Title (use style: paper title)

Data Forgery Images, Stock Photos & Vectors | Shutterstock

Cyber Forensic atau Computer Forensic adalah satu cabang ilmu forensik yang berkaitan dengan bukti legal yang ditemukan pada sistem komputer dan - PDF Download Gratis
KAJIAN IMPLEMENTASI CROSS SITE REQUEST FORGERY (CSRF) PADA CELAH KEAMANAN WEBSITE

Frequency Domain Analysis for Audio Data Forgery Detection | Semantic Scholar

Image Forgery Detection: Survey and Future Directions | springerprofessional.de




